My wonderful kids decided I needed a Sonic Toothbrush for Christmas. I wasn’t aware I did but I am enjoying it a lot. I noticed it had an RFID in the brush so of course I had to sniff it out with the flipper. It read and that lead to more investigations.

Looking at the brush you can see a gap in the washer and what looks like an RFID coil underneath. On the Flipper fb group someone said the chip was under there. That is what I would expect and it was not worth wrecking a new brush to find out. I will dissect it when I am done using it.

First test is can I emulate the chip back to the sonic? Nope.
Next up what does the data look like and what do we suppose is in it? Serial number, run time, maybe options. Let’s find out. The first read shows about half zeros with data scattered throughout
Filetype: Flipper NFC device
Version: 3
# Nfc device type can be UID, Mifare Ultralight, Mifare Classic
Device type: NTAG213
# UID, ATQA and SAK are common for all formats
UID: 04 52 80 82 14 74 80
ATQA: 00 44
SAK: 00
# Mifare Ultralight specific data
Data format version: 1
Signature: 66 81 F9 34 61 13 02 95 10 EE 49 C7 0A 82 5F D1 1F BB 41 66 F4 C1 F5 43 23 61 05 5D CB 53 F8 DE
Mifare version: 00 04 04 02 01 01 0F 03
Counter 0: 0
Tearing 0: 00
Counter 1: 0
Tearing 1: 00
Counter 2: 0
Tearing 2: 00
Pages total: 45
Pages read: 45
Page 0: 04 52 80 5E
Page 1: 82 14 74 80
Page 2: 62 48 FF FF
Page 3: E1 10 12 00
Page 4: 03 20 D1 01
Page 5: 1C 55 02 70
Page 6: 68 69 6C 69
Page 7: 70 73 2E 63
Page 8: 6F 6D 2F 6E
Page 9: 66 63 62 72
Page 10: 75 73 68 68
Page 11: 65 61 64 74
Page 12: 61 70 FE 00
Page 13: 00 00 00 00
Page 14: 00 00 00 00
Page 15: 00 00 00 00
Page 16: 00 00 00 00
Page 17: 00 00 00 00
Page 18: 00 00 00 00
Page 19: 00 00 00 00
Page 20: 00 00 00 00
Page 21: 00 00 00 00
Page 22: 00 00 00 00
Page 23: 00 00 00 00
Page 24: 00 00 00 00
Page 25: 00 00 00 00
Page 26: 00 00 00 00
Page 27: 00 00 00 00
Page 28: 00 00 00 00
Page 29: 00 00 00 00
Page 30: 00 00 00 00
Page 31: 00 01 0A 00
Page 32: 00 00 01 02
Page 33: 60 54 32 32
Page 34: 30 32 30 31
Page 35: 20 31 33 4B
Page 36: 75 01 00 01
Page 37: 00 00 00 00
Page 38: 00 00 00 00
Page 39: 00 00 00 01
Page 40: 80 03 38 BD
Page 41: 04 00 00 10
Page 42: 43 00 00 00
Page 43: 00 00 00 00
Page 44: 00 00 00 00
Failed authentication attempts: 0So let’s get before and after using images and compare them to see if anything changed. Aha, page 36 changed 2 bytes. I didn’t think to measure the time precisely but it was a couple minutes of “brushing”. I read it again and see 2 bytes changed. Assuming little endian by looking at the second byte going from 0 to 1 it comes out to 0xab or 171 or just under 3 minutes?
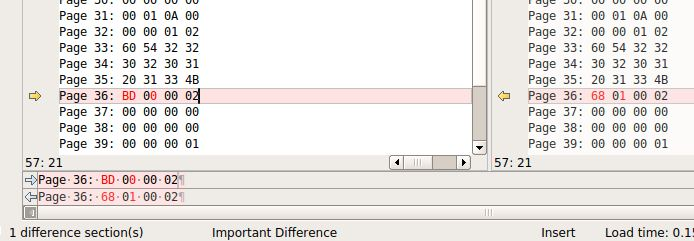
Let’s try it again for about 10 seconds and change the setting from GUM to WHITE. And we see a difference in our suspected run time counter of 13 which is close to 10 and the last byte of page 36 changed.

Let’s do it again and change from WHITE to CLEAN and also change the intensity from 1 LED to 3. And we see a similar 13 “seconds” change in the counter, the mode changed as expected and now byte 2 changed with the intensity as we might have predicted.

So now we know what Page 36 does. We could do more timing tests to see if there is an offset added each time or maybe it isn’t really seconds but something close to seconds?
The last comparison is between a new unused and this brush I have been using for 2 days . We would expect to see the run time counter at zero and a serial number somewhere and that’s exactly what we see, plus defaulted mode and intensity:

Plus the UID is different and the Signature, whatever that is. And it looks like Page is the serial number.
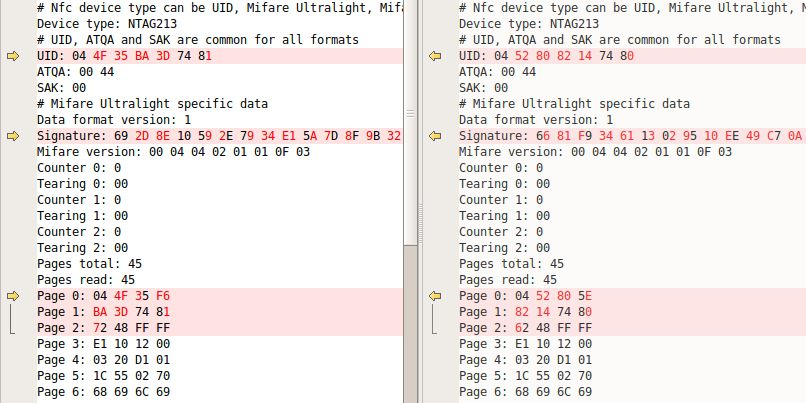
Here is the comparison to a GUM brush, assuming the first 3 pages are the serial number and expected to be different. Tooth on the left, Gum on the right. Page 36 we figured out are the user settings and time counter this opens up a bunch of new pages that are different. Any guesses?

So that’s it. Apparently the Sonic will work without having an RFID brush but without saving the settings between uses. It might be interesting to know why I couldn’t emulate it but I expect there is some security in the NTAG or Mifare preventing it. If anyone has an easy read on the formats let me know. I didn’t want to go on a deep dive today.
